Technology has covered almost all facets of today’s world.
From dusk to dawn, we are engaged digitally.From smartphones at home to meet all our daily needs, to make a fund transfer,
to order a refill of groceries, Everything is just a click away.
A typical day at the workplace involves dealing with connecting to intranet/internet servers.
A relaxed weekend at dine-in will involve the attendees taking customer’s orders through a tablet.
The customer is paying the bill through a Credit/Debit card.
All these transactions involve accessing the internet.
Hence it becomes important that everyone is aware of the risks of using digital data and its protection.
Online applications these days can be accessed through desktops, laptops, cell phones, etc.
These applications are highly interconnected.
Their ease of access makes them vulnerable.
For instance, Using the same cell phone, a user can update his status on a social media website.
He can transfer funds online at the next minute.
He/she might also use the same cell phone to access their personal identification details from the government database.
To top it all, he/she might use the same email account for registering in various banking, social networking applications, etc.
A weak password to this account is a temptation for hackers.
By gaining access to this email account, they might be able to access other applications linked with this account.
Also, spam mail can be sent through this account to lure a user into disclosing confidential information that might help the attacker to intrude into his/her banking application.
A vulnerable email account can make other applications vulnerable too.
What is Security?

No data is absolute security on the world wide web.
The quality or state of being secure
Cyber Security is the branch of computer science in which we study to secure internet-connected systems, including hardware, software, and data from cyber-attacks.
The CIA triad
Confidentiality –
Restrict access to authorized individuals.
Integrity –
Data is not modified in an unauthorized way. If somehow modification is done, it can be easily traceable(detectable).
Availability –
The information must be accessed and modified by authorized individuals. It should be done in an appropriate timeframe.
Confidentiality
“Need to know” basis for data access.
How do we know who needs what data?
Approach: access control specifies who can access what?
How do we know a user is a person she claims to be?
Need her identity and need to verify this identity
Approach: identification and authentication.
Ensuring authorized access to information assets when required.
The information has value if it is used by the right people at the right time.
We can say that an asset (resource) is available if:
- Timely request-response.
- Fair allocation of resources (no starvation!).
- Fault-tolerant (no total breakdown).
- Easy to use in an intended way.
- Provides controlled concurrency (concurrency control, deadlock control).
Data Integrity –
Primarily concerned with the accidental damage of data.
Prevention of unauthorized modification of information assets.
The Goal of Integrity is to stop and find unauthorized modification.
Integrity vs. Confidentiality
Concerned with unauthorized modification of assets (= resources)
Confidentiality – concerned with access to assets.
The thumb rules CIA triad.
Protect – Confidentiality
Preserve – Integrity
Promote – Availability
A customer wants to update his contact number on a website,
He clicks on the option provided on the website and receives an email to update his details.
However, this email was modified during transit by an unknown source, and two more personal data fields got added to the form to be filled up.
Businesses are increasingly leveraging new technologies such as mobile and cloud to enable strategic initiatives, and facilitate innovation.
Although these initiatives provide many business benefits, the new evolving technology landscape can also introduce substantial security risks that threaten sensitive corporate information.
The Security Triad:
Confidentiality ,Integrity,Availability
Physical Security & malware
Physical Security

- Who has access?
- Are sensitive documents secured?
- Are server and network area secure?
- Racks and Unmanaged Cables
- Opened Switch
Physical security is the protection of personnel, hardware, software, networks, and data from physical actions and events that could cause serious loss or damage to an enterprise, agency or institution.
Malware

Photo by Michael Geiger on Unsplash
What is malware?
“Malicious computer-executable”
A bit flexible definition-Annoying software or program codes.
Running code without a user’s consent.
Reasons for the increase
- Growing number and connectivity of computers
“everybody” is connected and dependant on computers,
the number of attacks increases,
attacks can be launched easily (automated attacks).
- Growing system complexity
unsafe programming languages, hiding code is easy.
verification and validation are impossible.
- Systems are easily extensible
mobile code, dynamically loadable modules.
incremental evolution of systems.
Types of malware:
- Viruses and Worms
- Spyware and adware
- Bots, trojans, and keyloggers
- Backdoors and DoS attacks
Virus & Worms

Worms are the oldest ones.
First, a well-known worm was known as the Morris Worm.
It used a BSD Unix flaw to propagate itself.
Viruses require hosts.
For example Word document, etc.
Both can spread through e-mail.
Melissa virus uses address books of the infected computers (1999).
This oldest form of malware is dying out.
Spyware & Adware

Growth of the Internet helped spawn spyware.
Largely fueled by the prospect of monetary gain.
It does not spread like viruses.
Instead, it is packaged with user-installed software (mostly p2p programs).
Least virulent forms cause sluggish systems, slow Web browsing, annoying pop-ups.
More dangerous spyware tracks browsing habits or sensitive information.
Bots & Trojans

Bots makers infect multiple systems
It creates massive botnets that can be used to launch a Distributed Denial of Service attacks.
The trojan is a way to secretly install a piece of malware on a system.
It could be an adware or a keylogger
It sneaks onto a system and delivers an unexpected and potentially devastating payload.
Structure of a virus
The infected program will first run the virus code when invoked.
If the infection phase is fast, then it will be unrecognizable.
The infected version of a program is longer than the normal.
A virus can compress the infected program to make its versions identical lengths.
Trojan Horse

TROJAN HORSE
It is another type of proper looking software but performs another action such as viruses.
It is usually encoded in a hidden payload.
Used in the installation of backdoors.
It does not propagate itself by self-replication.
Derived from the classical story of Trojan Horse.
Ransomware
RANSOMWARE
Ransomware is a kind of malicious code that targets the victim’s data by blocking access to the data.
In order to get the data unblocked, the victim might have to pay ransom to the attackers.
Simple ransomware may include locking the system.
Advanced ransomware uses cryptography techniques to block data access.
e.g. WannaCry etc.
Breaches & Common Cyber Attacks
Spamming

Spamming
Abuse of electronic messaging systems.
It is done to indiscriminately send unsolicited bulk messages.
It remains economically viable:
Advertisers have no operating cost beyond the management of their mailing lists.
Difficult to hold senders accountable for their mass mailings.
SPAM & SPIM

SPAM & SPIM
SPAM-Junk email.
SPIM- SPAM has come to Instant Messaging.
- Uncontrolled viewing (pop-up windows)
- SPIM is Bot generated
DDOS attack

DDoS ATTACK
DDoS attacks make computer systems inaccessible.
Achieved by flooding servers, networks, and end-user computers.
In a DDoS attack, a large number of compromised hosts are amassed.
If an attack comes from a single machine, it is referred to as a DoS.
Direct DDOS attack
An attacker can implant zombie software.
Master and slave zombies.
Attacker coordinates master zombies.
They trigger slave zombies
Note: Why are two-level zombies needed?
It makes more difficult to trace the attack back to its source.
Buffer Overflow
An application error occurs when more data is sent to a buffer than it can handle.
When the buffer overflows, the attacker can make the target system execute instructions.
The attacker can take advantage of some other unintended consequence of the failure.
Usually, the attacker fills the overflow buffer with an executable program code.
This elevates the attacker’s permission to that of an administrator.
Timing Attack

TIMING ATTACK
It works by exploring the contents of a web browser’s cache.
As many sites store the user credentials in the cache.
It can allow the collection of information on access to password-protected sites.
Another attack by the same name involves attempting to intercept cryptographic elements to determine keys and encryption algorithms.
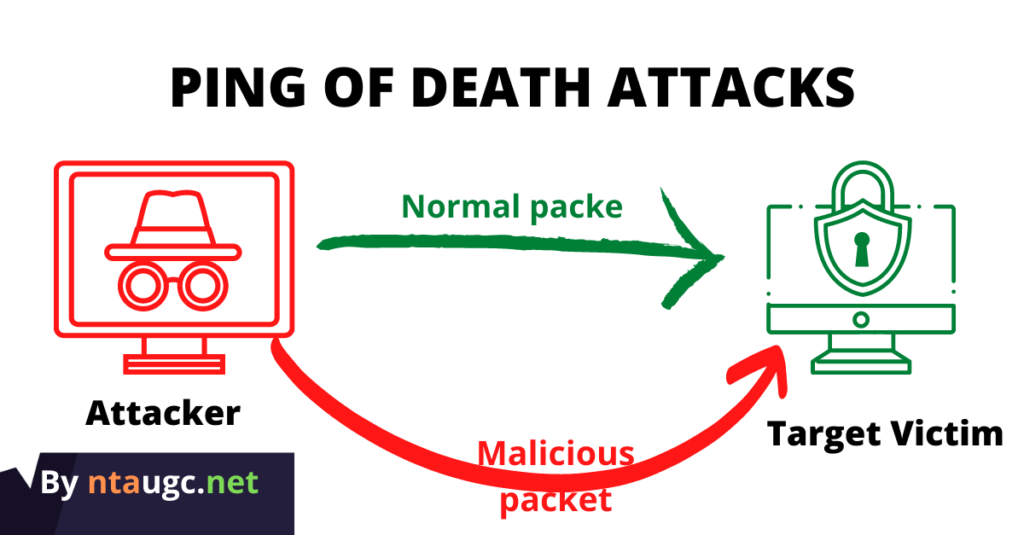
Ping of Death Attacks
PING OF DEATH ATTACKS
It is a type of DoS attack.
The attacker creates an ICMP packet that is larger than the maximum allowed 65,535 bytes.
The large packet is fragmented into smaller packets.
It is reassembled at its destination.
Destination user cannot handle the reassembled oversized packet.
Thereby causing the system to crash or freeze.
Other attacks:
Spoofing –
This technique used to gain unauthorized access.
The intruder sends messages to a computer with an IP address.
It indicates that the message is coming from a trusted host.
Man-in-the-Middle –
An attacker sniffs packets from the network, modifies them,and inserts them back into the network.
So at the destination, the user receives the altered packet. Integirty is voilated here.
Sniffers –
A program and/or device that can monitor data traveling over a network.
Sniffers can be used both for legitimate network management functions and for stealing information from a network.
Social Engineering –
Within the context of information security,
The process of using social skills to convince people to reveal access credentials or other valuable information to the attacker
Impacts of Cyber Crimes
Have you ever touched someone’s phone without permission?
Have you ever clicked someone’s photograph without their consent?
Well, if yes!.
You are a Cyber Criminal.
66E of IT ACT deals with the violation of privacy.
This chapter we’ll read about some such IT Acts & Cyber Laws.
Let’s get started.
NEED FOR CYBER LAWS & IT Acts
- TACKLING CYBER CRIMES
- INTELLECTUAL PROPERTY RIGHTS AND COPYRIGHT PROTECTION ACT.
- To provide legal recognition for transactions.
- To facilitate the electronic filing of documents with the Government agencies and E-Payments.
IT ACT PROVISIONS
- Email would now be a valid and legal form of communication in our country.
- It can be duly produced and approved in a court of law.
- Companies shall now be able to carry out electronic commerce.
- It can be done using the legal infrastructure provided by the Act.
- Digital signatures have been given legal validity and sanction in the Act.
- The Act now allows the Government to issue notification on the web thus heralding e-governance.
- a statutory remedy in case if anyone breaks into companies computer systems or network and causes damages or copies data
Types of cybercrime:
- CYBER CRIMES AGAINST PERSONS
eg ‘melissa and ‘love bug’ virus
- CYBER CRIMES AGAINST PROPERTY
eg computer vandalism
- CYBER CRIMES AGAINST GOVERNMENT
eg ‘Al-Qaeda’
Terms Related to Cyber Crimes
Forgery:
A forgery is a criminal act.
It takes place when a person falsifies something with the intent to deceive another person or entity.
Counterfeiting:
Counterfeiting crimes include various activities involving the production of fakes that are then presented in the place of genuine items.
For example,
someone knowingly selling cheap watches that actually say “Rolex” and use their trademarks is engaging in criminal activity.
Counterfeiting is a federal crime.
Identity Theft
Identity theft is a crime in which someone accesses information to commit fraud.
Typically by getting false credentials, opening new accounts in someone else’s name.
There are a lot of ways identity theft can happen to you.
Hackers may get your information from a data security breach.
Or, you may unknowingly provide it on social media That information may include:
- Social Security number
- Full name, address and birth date
- Credit card or bank account numbers
- Car insurance or medical insurance account numbers
- Details that can tip off people to your account-recovery questions, such as your mother’s maiden name or your home town
Tax Evasion:
Tax evasion is the illegal evasion of taxes by individuals, corporations, and trusts.
Tax evasion is an activity commonly associated with the informal economy.
Tax evasion usually entails taxpayers deliberately misrepresenting the true state of their affairs to the tax authorities to reduce their tax liability
Espionage or spying is the act of obtaining secret or confidential information without the permission of the holder of the information.
Spies help agencies uncover secret information.
Any individual or spy ring (a cooperating group of spies), in the service of a government, company or independent operation, can commit espionage.
The practice is clandestine, as it is by definition unwelcome.
In some circumstances, it may be a legal tool of law enforcement.
Espionage is a method of intelligence gathering which includes information gathering from undisclosed sources.
IT Acts & Cyber Laws
Now to handle these crimes,we have some Laws.
These Laws are under the IT Act 2000.
The Information Technology Act, 2000 provides legal recognition to the transaction done via electronic exchange of data.
Let’s see some basic sections of this act.
Section 65: Source Code
Whoever knowingly or intentionally conceals or alters any computer source code, is subjected to punishment under this section.
Ingredients:
- Knowledge or intention
- Concealment, destruction, alteration
- Computer source code required to be kept or maintained by law
Punishment:
- imprisonment up to three years and/or
- fine up to Rs. 2 lakh
SECTION 66 HACKING
- 66 Computer-related offenses.
If any person, dishonestly or fraudulently, does any act
- 66A.
Punishment for sending offensive messages through communication service, etc Publishing offensive, false or threatening information.
- 66B
Punishment for dishonestly receiving stolen computer resource or communication device.
- 66C
Punishment for identity theft -Whoever, fraudulently or dishonestly make use of the electronic signature, password or any other unique identification feature of any other person.
- 66D
Punishment for cheating by personation by using computer resources. Whoever, by means of any communication device or computer resource, cheats by personating
- 66E
Punishment for violation of privacy. Whoever intentionally or knowingly captures, publishes or transmits the image of a private area of any person without his or her consent, under circumstances violating the privacy of that person
- 66F
Punishment for cyber terrorism.
SECTION 70 Protected System
Ingredients
- Securing unauthorized access or attempting to secure unauthorized access to a ‘protected system’.
Acts covered by this section:
- Switching computer on / off
- Using installed software/hardware
- Installing software/hardware
- Port scanning
Punishment:
- Imprisonment up to 10 years and fine
- Cognizable, Non-Bailable, Court of Sessions
Why Cyber Security?

Why Cyber Security?
Cyber attacks are a great threat to the global economy and to our personal data.
There are two important aspects that needs to be protected:
- Information: Customer’s data, source code, design documents, financial reports, employee records, intellectual property, etc.
- Information systems: Computers, Networks, cables, etc.
A good Cyber security approach plays a vital role in minimizing and controlling damage.
Also recovering from a Cyber-breach and its consequences.
Let us understand more about what Cyber Security is.
Cyber Security is a set of techniques used to protect systems, networks, and applications.
It works against attacks, damage or unauthorized access emerging from internet.
These attacks are usually aimed at
- accessing, changing, or destroying sensitive information.
- extorting money from users.
- interrupting normal business processes.
The implementation of effective Cyber Security measures is a challenge in today’s world.
Each of the Cyber attacks violates one or more Security Objectives that are listed below.
- Confidentiality
Makes sure that data remains private and confidential.
It should not be viewed by unauthorized people through any means.
Information disclosure is a cyber attack that reads all emails sent to/by the victim by eavesdropping into the communication network, hence, compromising confidentiality.
- Integrity
Assures that data is protected from accidental or any deliberate modification
Tampering is a cyber-attack where attacker modifies an incoming email before it reaches the intended recipient.
The receiver would not know that the received message was modified, hence, compromising the integrity
- Availability
Ensures timely and reliable access to information and its use
Denial of service is a cyber-attack where the website becomes unavailable for legitimate users, restricting the availability of the website
Confidentiality, Integrity, and Availability are together called as CIA.
Disclosure, Alteration, and Denial (DAD) is an alternate way of referring to the CIA.
Authentication, Authorization, and Accounting (AAA) are three important services that support these Security Objectives.
- Authentication
Authentication is verifying an identity
Spoofing is a kind of cyber attack.
In an attacker impersonates an authentic user of a particular website, compromising the authentication of that website.
- Authorization
Authorization is determining whether a particular user is allowed to access a particular resource or function
Elevation of privilege is a kind of cyber attack.
In it an attacker accesses the functions which he/she is not allowed to access, hence, compromising authorization.
- Accounting (Non-repudiation)
Recording a log of activities of a user in a system is known as auditing
Accounting refers to reviewing the audited log file to check for violations.
Hold users answerable to their actions.
It includes non-repudiation
Repudiation is a kind of cyber attack.
In it, an attacker performs an attack and later deny performing it
Having learned about the objectives and services of Cyber Security,
let us get familiar with other commonly referred Terms of Cyber Security.
What needs to be secured?
Any IT organization comprises of the following security layers.
- Information Security-
It is about protecting the information that is valuable to the organization.
It is about the protection of information in all its forms – electronic, printed, hand written, verbal etc.
This applies to all aspects of safeguarding or protecting data, in whatever form within the organization
E.g. protection of intellectual property, trade secrets, email communications, blood group of employees, etc from being leaked or tampered
- Network Security-
It is about ensuring the availability of networks and confidentiality and integrity of data flowing within the network.
The organization’s network is a trusted zone.
Traffic entering the Intranet (trusted zone) from the Internet (untrusted zone) must be carefully scrutinized.
There should be mechanisms to prevent malicious traffic from entering the network
E.g. use of a firewall to control all inbound and outbound traffic in the network
- Host (Operating System) Security-
It is about protecting the Operating System from malware, hacker intrusion etc. by adapting preventive measure.
The basic aim of OS security is to safeguard the assets of a computer.
As these assets can be capable of being altered, deleted or hacked
E.g. installation of the antivirus.
- Application Security –
It is ensuring that the web applications are developed following the secure design.
It involves preventing the security bugs and flaws in any application.
E.g. building applications that follow secure coding guidelines, etc.
- Human (People) Security –
It is about creating and leveraging awareness among employees.
Becoming cautious about sharing sensitive information, downloading an attachment from unauthorized sources and handling organization’s resource as per policies
E.g. protecting organization from phishing emails by creating awareness among the employees, etc.
Terms related to Cyber Security
Apart from the CIA objectives and the AAA services, there are some more terminologies quite frequently used in the Cyber Security space.
- Asset
- Vulnerability
- Exploit
- Threat
- Threat Agent
- Risk
- Attack Vectors
- Control
Let us understand each of these through examples.
- Asset
The term ‘asset’, in general, refers to a valuable possession of an individual or an organization.
In cybersecurity space, asset refers to the hardware or software holding confidential data, IT networks, etc.
This needs to be protected from being altered, deleted or misused by an attacker.
- Information asset
Information or data that has economic value to the organization is termed as an Information asset.
It has the following features:
It is a part of the organization’s identity
It may be highly confidential(top secret)
Information about people and procedures
Software or hardware details
Networking elements
E.g. Confidential emails, identity information, system data, bank transactions, newly developed design schema of a project, etc are a few to be named under information assets of an organization.
- Vulnerability
Vulnerability refers to the state of weakness of being exposed to potential attacks.
E.g. Software bugs, Inefficient controls, Hardware flaws, Human errors
- Exploit
Exploit refers to a piece of code that takes advantage of a vulnerability in computer hardware or software to cause unexpected behavior in them.
E.g. Computer virus, malware or flooding of requests to the server by a bot.
- Threat
The threat is any potential danger that is associated with the exploitation of a vulnerability.
A threat is an undesirable event that can happen to assets.
E.g. An organization running on windows operating system was targeted and blocked until a ransom of $300 was credited to hackers to unlock the data.
The threat here is the leak of data.
- Threat agent
A threat agent is a term used to represent an individual or group that can cause a threat.
It is important to identify who would want to exploit the assets of a company (capabilities), and how they might utilize those (intentions) against the company.
E.g. The threat agent in the above example is a hacker.
- Risk
Risk is the probability of causing damages to an asset by a threat agent.
The threat agent exploits the asset’s vulnerabilities.
This eventually can have a substantial impact on the organisation.
There are many paths by which a threat agent can exploit the vulnerability of a system.
The paths taken to exploit could be easy or hard .
The harm that is caused by them may lead to any or no consequence.
These paths are commonly known as attack vectors.
- Control
Control is mitigation to protect the asset from risks.
E.g. Some organizations would not have faced the WannaCry ransomware attack if the latest OS patches were updated in time.
Note: You can refer to the Common Vulnerability Scoring System (CVSS) for risk calculation. It is a free and open industry standard for assessing the severity of computer system security vulnerabilities.
Network Security

network security
Network security refers to any activity taken to protect the availability of networks, confidentiality and integrity of data in the network.
The internet is an untrusted place.
Anything coming from it could be potentially harmful.
The organization’s network is a trusted zone.
Data entering the intranet (trusted zone) from the Internet (untrusted zone) must be carefully scrutinized.
There should be mechanisms to prevent certain data from entering the network
How is Network Security Achieved?
It is achieved by using important security devices that perform the scrutinization.
- Firewalls
- Intrusion Detection Systems (IDS)
- Virtual Private Network (VPN) gateways
What is a firewall?
A firewall is a special computer that is placed between an organization’s intranet and the Internet.
All communication between the internet and the intranet flow through this firewall.
A firewall has an access control list like the one shown below.
Each entry in it is called a Rule.
The firewall inspects every packet’s headers – source and destination IP addresses, ports, etc
It compares the header information with each rule in the access control list, in an if-elseif-else way
If a packet matches a particular rule then, the action specified under that rule is applied
The action could be to allow or deny entry/exit for a packet
Apart from controlling access to internet sites,
a firewall is used to block several types of attacks like DDoS.
And to enforce an organization’s network policy (E.g. Employees are not allowed to access specific Internet websites).
What is intrusion?
An unauthorized user logs on to a machine
An authorized user disables logging functionality in a router
A worm (a type of malware) spreads to all the hosts in the network
An authorized user (say an employee) downloads all employee directory records to his computer
An unusually high number of login attempts in a host
All the above examples involve a user (or computer process) trespassing or attempting to trespass into a network (or host).
Such actions are called intrusions.
A firewall cannot be useful in detecting or stopping such intrusions.
An Intrusion Detection System (IDS) is used to detect such intrusions.
What is an IDS?
An IDS is dedicated computer or a software running on a general purpose computer.
It is positioned at certain points in the network.
The IDS sniffs all the packets at that point.
It analyses the contents of network packets (headers and application data) and the sequence of packets
If analysis result indicates an intrusion, an alert message is sent to the administrator
An IDS can also use different log files (generated by hosts) as input for detecting intrusions
What is a VPN?
A VPN is an extension of a private network across a public network.
It enables the users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network.
Benefits of using VPN:
- Access a business network while traveling
- Protect yourself from snooping on untrustworthy Wi-Fi hotspots
- Get connected to organization’s network securely
Operating System Security
OS security is the process of upholding security objectives such as Confidentiality, Integrity and Availability of the system.
OS security measures are taken to protect the Operating System from threats such as virus, malware and remote hacker intrusions.
Threats emerging from access to OS are of two types.
- Intruder
- Malicious software
Intruder
Individuals who exploit and penetrate a system’s access controls
A legitimate user who is not authorized to access certain data or programs
An individual who controls the supervisory access of system and begins to play with files or data present in the system
Malicious Software
These are software programs which exploit vulnerabilities in a computer system.
They can be divided into two types.
- Parasitic – Fragments of programs that cannot exist independently of some actual application program, utility, or system program. e.g. Viruses, logic bombs, and back doors
- Independent – Self-contained programs that can be scheduled and run by the Operating system. e.g. Worms and bot programs
Hence its important to protect the Operating System from these threats.
How is Operating System Security Achieved?
Operating System security may be approached in many ways. Some of which are listed below.
- Regular Updates
Update Operating System with latest patches to fix any known vulnerability
Install updated antivirus engines and software to combat the latest threats
- Ensure Proper Access Control
Ensure least privileges are assigned to users
- Operating System Vulnerability Assessment
Detect vulnerabilities in Operating System using appropriate tools and mitigate it.
Basics of Digital Forensics
WHAT IS FORENSIC?

WHAT IS FORENSIC?
Forensics is the art of acquiring and analyzing information obtained from a computer or smartphone in a legal way.
It includes smart devices and would encompass IoT in the future.
Forensics required to:
- Recover lost data – inadvertent or purposeful deletion
- To investigate cyber crimes
- Prevent cyber frauds
- Financial and IPR safeguards
- Incidence Response
WHY FORENSICS?
- Smartphones are an indispensable piece
- IoT is the driving force
- Every device is becoming smart
- Huge warehouse of information
- Protection of personal data
- Law enforcement
- Data stealing malware
AREAS OF FORENSICS
- Computer Forensic
- Mobile devices Forensic
- Network Forensic
- Database Forensic
- IoT(internet of things) Forensic
FORENSIC PRINCIPLE
Digital/ Electronic evidence is extremely volatile.
Once the evidence is contaminated it cannot be decontaminated.
Chain of Custody is crucial.
When dealing with digital evidence, all of the general forensic and procedural principles must be applied.
Upon seizing digital evidence, actions taken should not change that evidence.
All activity relating to the seizure, access, storage or transfer of digital evidence must be fully documented, preserved and available for review.
Forensic analysis should be performed on the cloned suspect drive instead of original suspect device.
Valunarability is the art of acquiring and analyzing information obtained from a computer or smartphone in a legal way.
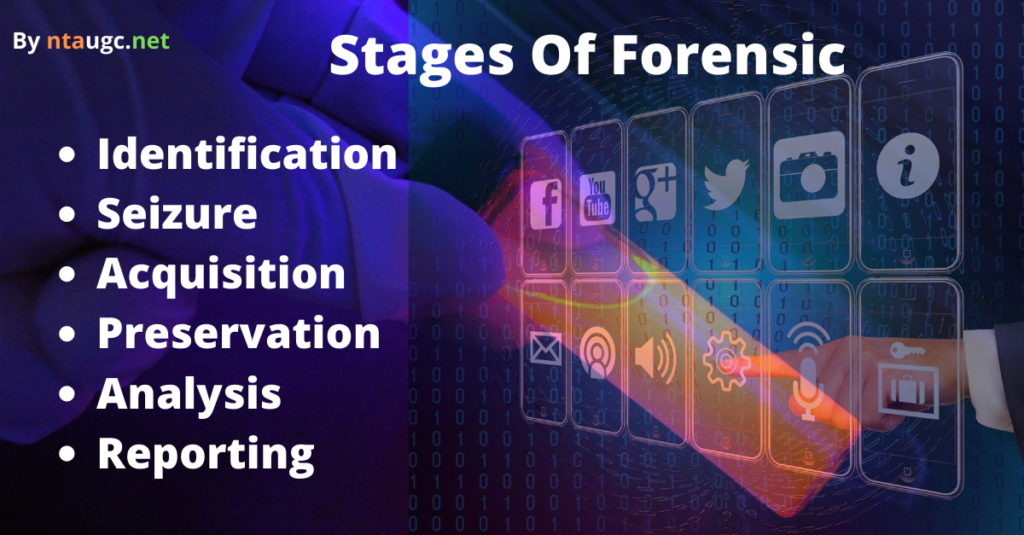
Stages of Forensic
Stage Of forensics
Stages of Forensics include
- Identification
- Seizure
- Acquisition
- Preservation
- Analysis
- Reporting
- Identification
The first step is identifying the evidence as per system details and the other peripheral devices identify the compromised system(computer, mobile devices).
Taking note of OS details, HDD details.
Identifying the peripheral devices of the systems.
- Seizure
The seizure is carried out on the crime scene.
If the system is switched off never boot it.
Take RAM dump of the system if it is in live or switch on condition.
check the other peripherals of the system.
Directly pull the power cable from the system after taking RAM dump and protected files
Fill the chain of custody form and bring out the system to the forensic lab.
Chain of Custody
The term “chain of custody” refers to documentation that identifies all changes in the control, handling, possession, ownership, or custody of a piece of evidence.
You need to be able to trace the route that evidence takes, from the moment you collect it, until the time it is presented in a court of law.
Documentation of date,time, case number , HDD details, device information, RAM dump information.
Details of any other peripheral devices.
Majorly done to check the integrity of the evidence.
- Acquisition
The acquisition process usually consists of creating a bit-by-bit copy(cloning) of the digital media evidence.
Cloning of suspect drive and capture the hash value(MD5, SHA256, SHA1).
- Analysis
The analysis depends on the specifics of each job
Static Analysis
Dynamic Analysis
Tools using ftk, Encase, Autopsy, recovery tool(Easeus data recovery, Steller phoenix)
Analysis of peripheral devices like modem, mobile,PDA etc is done.
- Reporting
Prepare a report with all the evidence found during the analysis.
Place all the evidence with snapshots.
Present the findings in a very technical and simplistic manner.
Myth bursting
Myths about Cyber security
There are a lot of myths that are commonly associated with Cyber Security which are very different from the facts.
Myth 1: “Digital and physical security are separate systems”
Reality:
The world is moving towards automation and artificial intelligence.
Most physical devices such as Biometric systems, CCTV cameras, and controlled digitally.
Hackers can affect even physical infrastructure causing catastrophic levels of damage to physical resources.
Myth 2: “Cybersecurity is just an IT issue”
Reality:
Once data is digitized, it has to be protected whether it is in the data center or employees’ mobile phone.
Myth 3: “Protecting yourself is good enough.”
Reality:
Organizations must have an eye on everything and everyone.
Third parties from subcontractors to subsidiaries, vendors and accounting firms, etc. can be a threat vector.
Myth 4: “Going back to paper minimizes risk.”
Reality:
One can’t know if paper copies of data have been unlawfully copied or removed.
Myth 5: “Using antivirus software is enough.”
Reality:
Hackers have found multiple ways to intrude into antivirus software.
In many cases for an average of six months.
With the advent of ransomware, the time frame from infection to damage has become almost instantaneous.
Myth 6: “We have a firewall. We’re in good shape.”
Reality: Firewall is used to allow expected traffic in and restrict all remaining traffic.
This is done by creating Access Control Lists (ACLs).
However, most cybersecurity assessments depict that the greatest cyber threats are associated with the behavior of authorized users of the systems allowed inside the firewall.
Hence, it’s important to understand what needs to be secured.
As we know by now, Cyber Security is not just about installing the latest anti-virus, Or have a strong firewall.
It is ensuring that all the aspects of your organization are well secured.
Conclusion
Cybercrime prevention
- Use strong passwords
- Secure your computer
activate your firewall
use anti-virus
block spyware attacks
- be social – media safe
- Secure your mobile devices.
- Install the latest OS.
- Secure wireless network.
- Protect your e-identity
Cybercrime greatly affects individuals, businesses, and national security due to the pervasiveness of the internet.
Different countries should work together and use legal, organizational, and technological approaches to combat cybercrime.
To reduce the damage to critical infrastructures.
To protect the internet from being abused.

















